$55m Funds Lost in May 2023: Top DeFi Scams and Exploits
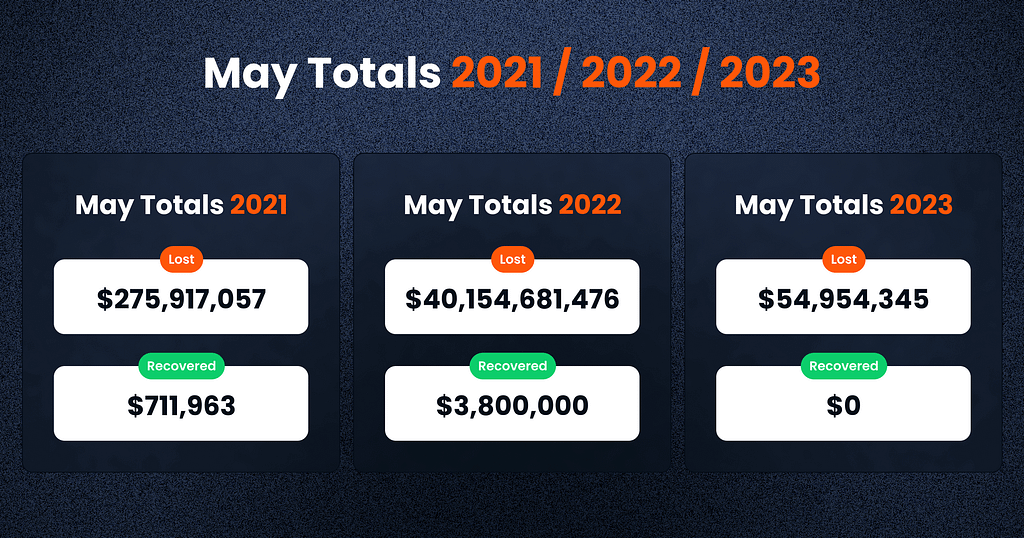
In May 2023, the cryptocurrency market experienced significant losses, with a total of $54,954,345 reported as funds lost.
Unfortunately, no funds were recovered during this month. The majority of the losses were attributed to the Binance ecosystem, with a total of $37.1m reported across ten cases.
In May 2023, the DeFi space experienced a series of scams and hacking incidents, resulting in significant losses. The total amount lost this month reached $55 million, a notable decrease compared to the same period last year when losses amounted to a staggering $40 billion. This is also considerably lower than in April, where $101.5 million was lost.
Although the decrease in losses is encouraging, this figure remains a reminder of the ongoing challenges faced by the DeFi industry in ensuring platform security. Efforts to enhance security measures and raise awareness about fraud and scams seem to be producing positive outcomes.
Regrettably, no recoveries were made in May 2023. The recovery of funds remains a crucial aspect in mitigating the impact of losses and restoring confidence in the DeFi ecosystem.
DeFi Exploit Trends: May 2023 Overview
The cryptocurrency landscape in May 2023 witnessed a significant amount of funds lost, totaling $54,954,345. Binance remained a prime target for these incidents, with six cases reported and a total loss of $37.1m. Another hotspot, the Ethereum Chain experienced ten cases, resulting in $2.1 in losses.
Among the top 10 cases, DFintoch suffered the highest loss of $31.7m due to a smart contract exploit. Jimbo Protocol on Arbitrum experienced a loss of $7.5 as a result of a rugpull, while Deus Finance on BNB lost $6.2 in a smart contract exploit.
Tornado Cash, on the Ethereum blockchain, also suffered a loss of $1,049,513 due to an exploit. Other notable cases include Mother, WSB Coin, Linda Yaccarino, Block Forest, SNOOKER, and land, with losses ranging from $145,043 to $733,883.
Types of Exploit
In May 2023, various types of exploits were employed by cryptocurrency criminals. However, rug pulls continued to be the most prevalent, accounting for 12 cases and losses totaling $36.9m.
9 cases of exploits have taken place, resulting in losses amounting to $8.8m. Flash Loan Attacks, although less frequent with 5 cases, still led to significant losses totaling $8.9m.
Other exploit types, such as access control issues, phishing, and oracle issues, were not reported during this period. However, 2 cases of exit scams resulted in a loss of $177k.
Funds Recovered
In May, no exploited funds were recovered, continuing the unfortunate trend of low recovery rates in recent months. This highlights the importance of improved security measures and investor vigilance in the DeFi space.
Attack Vectors
Among the different categories of targets, tokens were the most commonly attacked, with 19 cases reported and losses totaling $3.3m.
Borrowing and Lending protocols experienced no reported losses during this month. Decentralized Exchanges (DEX) were targeted in 3 cases, resulting in losses of $4m.
Notably, Stablecoins were the category with the highest amount lost, amounting to $6,227,977 in a single case. Other categories, including CeFi (Centralized Finance), Yield Aggregators, Gaming & Metaverse, and NFTs, did not report any losses during this period.
Top Exploits in May 2023
Let’s take a look at the top 5 cases this month:
1. DFintoch — $31.7m Lost (Rug pull, 22 May)
The DFintoch project deployed the FintochSTO contract using the deployer address 0x8a0deffb71a5dc17a779ab25fdc17fdeb249aa63. During deployment, 100,000 FTH tokens were minted. These tokens were then sent to address 0xfce4d. However, on the May-22–2023, a transfer of 34,341 FTH tokens was made from 0xfce4d to address 0xec1a.
Following that, 20,000 FTH tokens were swapped for 31,666,317 USDT using the “swapForUSDT()” function on the contract with address 0x19a00e359990ec7daf6e9dd9a2fb7664014bb5f7.
The funds were subsequently moved to address 0x398dcb3e535f701e93ed2891aaab601c25ebacf4. Multichain and SWFT were utilized for the bridging of funds.
Block Data Reference
Transaction deploying FintochSTO contract: https://bscscan.com/tx/0x3ef479ba75e07ad04f02b5a5f4df476bbbc83bb5d15fdcd2acd1955a4e87fce6
Transaction transferring 34,341 FTH to address 0xec1a:https://bscscan.com/tx/0xee053bf3c429603319d352979e09b207103a08ebf5f42aa0ddd22a9d67f004d6
SwapTx: https://bscscan.com/tx/0xa5e64161928ee40f6af02a32fc5c1fb9efa05cca6b91d88326279329b71c7ea2
2. Jimbo Protocol
The attack on Jimbos Protocol exploited the lack of slippage control on liquidity conversions, allowing the attacker to reverse swap orders and benefit from the price discrepancy. The protocol’s mechanism, designed to address liquidity and volatile token prices, had a logical vulnerability that enabled the exploit. As a result, the price of the native token, Jimbo (JIMBO), dropped by 40%. The attackers extracted 4,090 ETH from the Arbitrum network and used the Stargate bridge and the Celer Network to transfer around 4,048 ETH from the Ethereum network.
Block Data Reference
Exploit tx:https://arbiscan.io/tx/0x44a0f5650a038ab522087c02f734b80e6c748afb207995e757ed67ca037a5eda
Exploiter: https://arbiscan.io/address/0x102be4bccc2696c35fd5f5bfe54c1dfba416a741
Bridged funds:https://etherscan.io/address/0x5f3591e2921d5c9291f5b224e909ab978a22ba7e
3. Deus Finance
DEI is a stablecoin of Deus Finance which lost its dollar peg on the previous hack. On May 5th, 2023 Deus Finance’s $DEI token was exploited due to a logic flaw related to burn issue that allowed an attacker to drain DEI/USD and DEI/USDC pools on both Arbitrum and Binance Smart Chain (BSC) chains. The attacker performed zero-amount burns and received $DEI tokens for nothing, which was consequently swapped for valuable stablecoins. On BSC chain alone roughly 1,336,814 $USD was lost. The stolen funds were transferred through several EOA addresses and then swapped for $DAI. And 4,891,163 $USD were drained from the Arbitrum chain and swapped for 2,529 $ETH, which remain at the same address.
The attack resulted in a total loss of approximately 6,227,977 $USD worth of crypto assets from both chains combined.
Block Data Reference
Attacker initial address in BSC: https://bscscan.com/address/0x08e80ecb146dc0b835cf3d6c48da97556998f599
Funds holder address in BSC: https://bscscan.com/address/0xdf61022837de1126488ed80f179eedd7af9cb465
Malicious transaction in Binance Smart Chain: https://bscscan.com/tx/0xde2c8718a9efd8db0eaf9d8141089a22a89bca7d1415d04c05ba107dc1a190c3
Attacker initial address in the Arbitrum chain: https://arbiscan.io/address/0x189cf534de3097c08b6beaf6eb2b9179dab122d1
Malicious transaction in the Arbitrum chain: https://arbiscan.io/tx/0xb1141785b7b94eb37c39c37f0272744c6e79ca1517529fec3f4af59d4c3c37ef
4. Swaprum — $2.9m Lost (Rugpull, 18 May)
Swaprum, an Arbitrum-based decentralized exchange (DEX) project, recently fell victim to a rugpull orchestrated by its own deployer. The rugpull resulted in a substantial loss of funds, totaling 2,915,567 USD. The exploit involved privileged access to liquidity providers (LPs) across multiple pools and the unauthorized minting of the project’s native token, $SAPR.
The rugpull consisted of two main components. Firstly, the deployer executed liquidity removals from various pools, including USDT/WETH, USDT/USDC, ARB/WETH, ARB/USDC, WOM/USDT, and more. These removals amounted to approximately $951,000 in losses, depleting the liquidity in these pools.
The second part of the exploit focused on the $SAPR token itself. The deployer initially minted 800,000 $SAPR tokens directly into their wallet address. Subsequently, an additional 500,000 $SAPR tokens, along with approximately $94,000 worth of WETH, were drained from the SAPR/WETH pool. This malicious action left the pool completely emptied of liquidity.
To compound the damages, the attacker deployed a malicious upgrade for the SAPR Controller Proxy contract. This upgrade enabled the creation of an additional 200 million new $SAPR tokens through two separate transactions, effectively diluting the value of existing tokens and harming legitimate token holders.
The total loss resulting from the rugpull amounted to 2,915,567 USD. The stolen funds were then transferred to another externally owned account (EOA) address in two transactions, which equated to 1,617.7 ETH. The attacker utilized various techniques to obfuscate the movement of the stolen funds, including utilizing privacy-focused tools like TornadoCash and bridging assets through platforms such as Celer Network and Multichain Bridge.
Block Data Reference
Scammer address:
https://arbiscan.io/address/0xf2744e1fe488748e6a550677670265f664d96627
Fund holder address:https://arbiscan.io/address/0xaaf8b44376f4ef3ed477eeeb3553b7623fef5e1c
Liquidity removal transaction examples:
https://arbiscan.io/tx/0x0ebc5f9108974f5518cee002ab7dc4cfed6affb8e5f83ad430bfb00431f0c3be
5. Level Finance — $1.1m Lost (Exploit, 1 May)
Level Finance, a decentralized perpetual exchange operating on the Binance Smart Chain, fell victim to an exploit that resulted in a significant loss of funds. The exploit specifically targeted the Referral Controller Contract, enabling the attacker to claim referral amounts in the form of $LVL tokens multiple times, ultimately draining the contract of 214,000 $LVL tokens. The stolen tokens were subsequently exchanged for 3,345 BNB, which amounts to approximately $1,097,160 USD at current market prices.
The attack was orchestrated by an individual operating from the address 0x61bb…412e. The stolen funds are currently held under the control of the attacker at the address 0x7031…a9d5. It is worth noting that this exploit exclusively targeted the Referral Controller Contract, and other entities such as LPs (liquidity providers) and the DAO treasury remained unaffected, as the attack was isolated from other contracts within Level Finance.
Attacker Address:
https://bscscan.com/address/0x61bbd8c1bc09c4f4549f3f77be5ad61a9929412e
Funds Holder Address: https://bscscan.com/address/0x70319d1c09e1373fc7b10403c852909e5b20a9d5
Malicious Contract Address: https://bscscan.com/address/0xf08a01d2cace301ae69f07af5fdfb2336da2f629
Affected Proxy Contract Address: https://bscscan.com/address/0x977087422c008233615b572fbc3f209ed300063a
Affected Implementation Contract Address (LevelReferralControllerV2): https://bscscan.com/address/0x9f00fbd6c095d2c542687ed5afb68d9c3fb2f464
Conclusion
The scale of monetary losses during May 2023 underscores the importance of heightened risk management and attentiveness when engaging with the decentralized finance (DeFi) industry. It is crucial for investors to familiarize themselves with potential risks and implement suitable strategies to safeguard their investments. Here at De.Fi, we recognize the significance of offering support in navigating the intricate and dynamic DeFi ecosystem. Consequently, we are committed to providing our users with valuable tools and information to enable well-informed investment choices within the sector.

Right now we are GIVING AWAY free copies of Security Bibles — the most comprehensive DeFi Security Guide brought to you by the De.Fi Team!